In the last post about the Observable Universe, I discussed the sheer scale of the cosmos and that mind-bending 46.5 billion light-year edge. But as I kept digging into how we actually measure that expansion, I stumbled into a conflicting opinion among the astronomers. This made me further explore the Hubble Tension, and now I finally understand why astronomers might be freaking out.
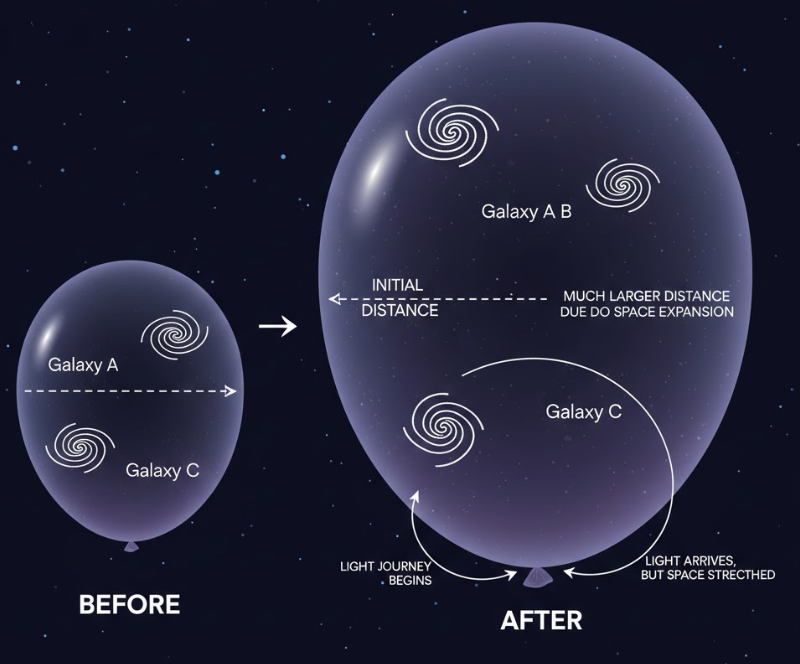
The universe is currently presenting us with two different answers to the same basic question: “How fast are we growing?” During my school days, I studied Hubble’s Law, which states that “galaxies are moving away from Earth at speeds proportional to their distance, providing key evidence for the expansion of the universe.” In 1929, Edwin Hubble proposed the Hubble constant, which quantifies the rate of the universe’s expansion. This constant can be measured by observing the distances of celestial objects and the speeds at which they are moving away from us.
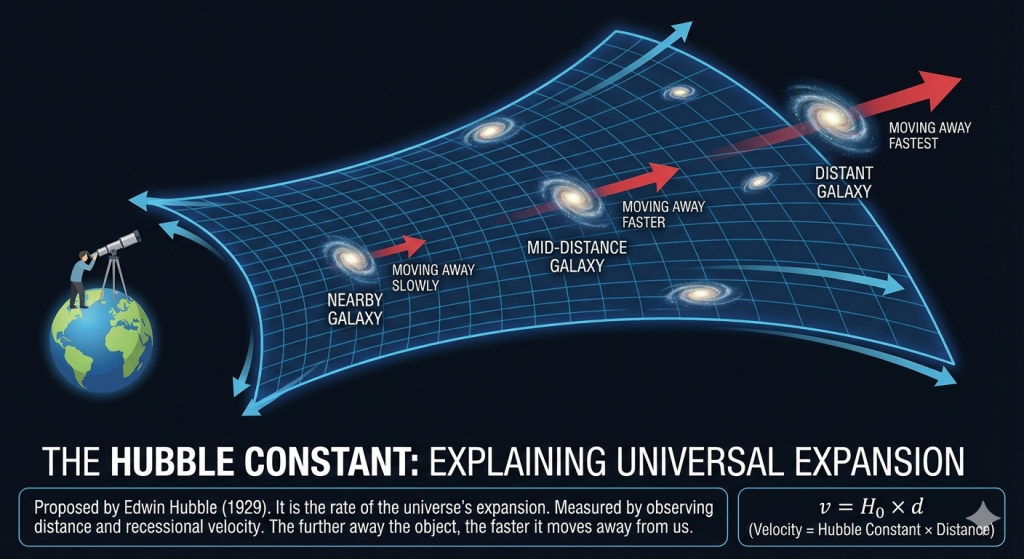
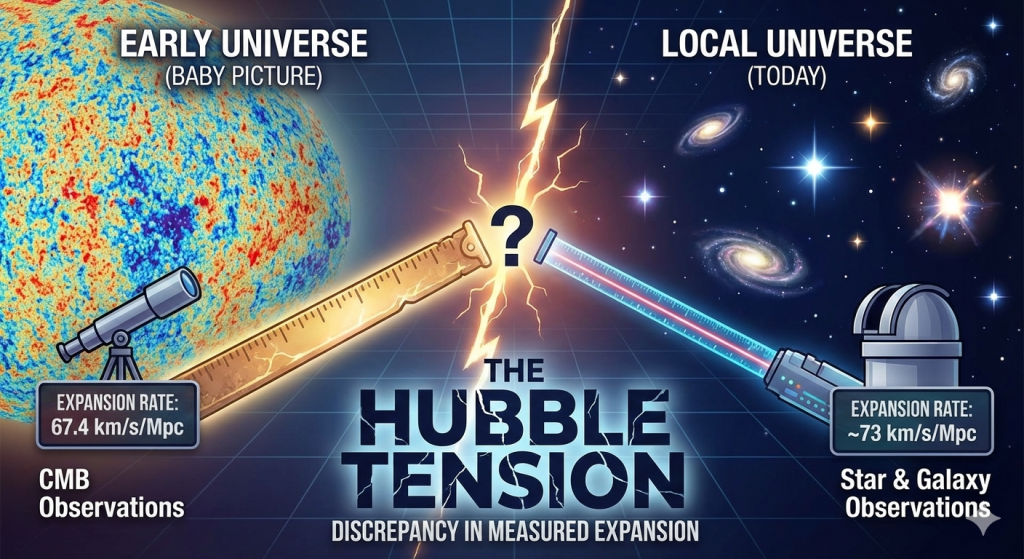
We have two primary methods for measuring the Hubble Constant. Currently, these two methods are at a standoff. To keep things simple while I was wrapping my head around this, I started calling them the “Baby Picture” team and the “Local” team“.
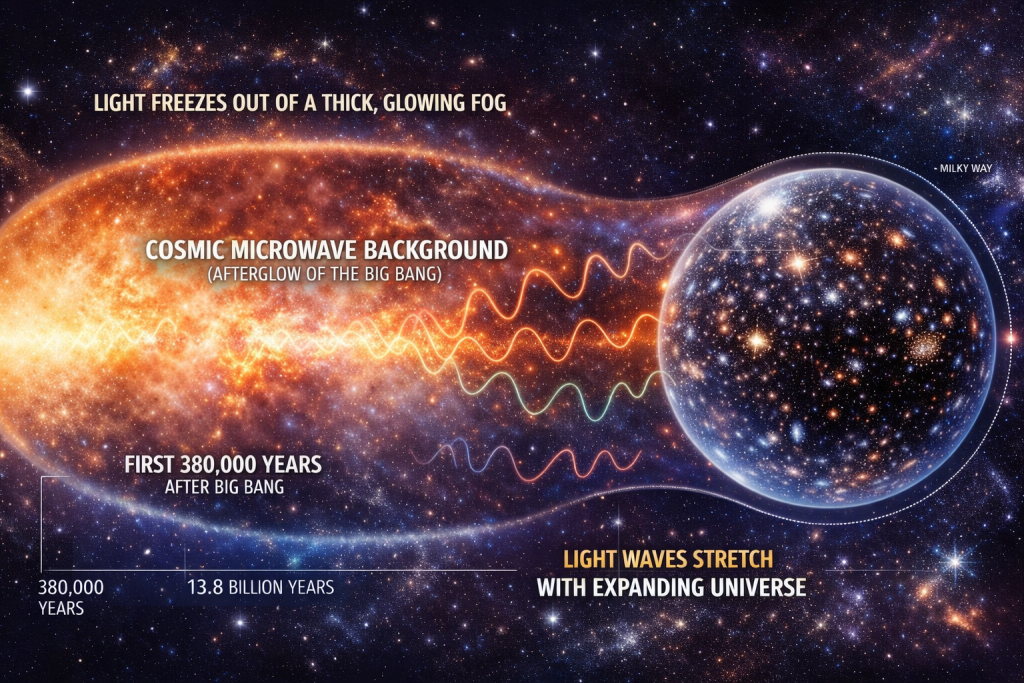
On one side, we have the “Baby Picture” Team (which scientists formally call the Early Universe or CMB measurements). They look at the Cosmic Microwave Background, the afterglow of the Big Bang, to calculate how fast the universe should be expanding based on its initial conditions. Their math gives us a speed of 67.4 km/s/Mpc.
On the other side, there’s the “Local” Team (officially known as the Late Universe or Distance Ladder measurements). Instead of looking at the beginning of time, they look at what’s happening right now, measuring actual stars and galaxies in our neck of the woods. Their measurement comes in much higher, at roughly 73 km/s/Mpc.
A gap of five or six units might not seem like a big deal, but in the world of physics, it’s a total disaster. It’s like two people measuring your height: one insists you’re 5’8″ and the other is positive you’re 6’1″, and both are certain their tape measures are perfect.
This disagreement is what scientists call the Hubble Tension. It’s the ultimate “it doesn’t add up” moment, creating a massive conflict between the “blueprints” we see in the early universe and the “finished house” we see in our local neighborhood today.
I found a paper published in January 2025 titled “The Hubble Tension in Our Own Backyard: DESI and the Nearness of the Coma Cluster, ” which addresses the ongoing debate about the expansion rate of the universe. The research team, led by Dan Scolnic, used the Dark Energy Spectroscopic Instrument (DESI) to obtain the most precise measurement to date, 76.5 km/s/Mpc. This measurement is even faster than previously anticipated. As a result, it effectively rules out the possibility of measurement error. This indicates that the universe around us is definitely expanding faster than expected.
| NOTE In the post, the term km/s/Mpc is used. “Mpc” just stands for Megaparsec, which is about 3.26 million light-years. One parsec is 3.26 light-years. Think of it like a speed-per-distance rule. If the rate is 73 km/s/Mpc, it means a galaxy located at 1 Megaparsec away is moving at 73 km/s, while a galaxy twice as far away is moving at 146 km/s. The further out you go, the faster the “stretch” happens! |
Are We Currently in a Bubble?
So, if the measurements aren’t wrong, what is?
To answer this, when I further searched on the net, I came across a groundbreaking new study from the Royal Astronomical Society titled, “Earth Inside Huge Void May Explain Big Bang Expansion Rate Puzzle“, which suggested that the problem is not the math, it’s our own address, where we live.
To understand this better, let us think of it as a giant game of cosmic tug-of-war. Usually, matter is spread out evenly, so everyone is pulling on each other with equal strength. But because we live in a ‘void’ (an empty pocket), there are way fewer people on our side of the rope. Meanwhile, the rest of the universe outside our bubble is packed with matter. Because they have more ‘players’ (more gravity), they are pulling galaxies away from us much harder and faster than they normally would. From our perspective in the middle, it looks like everything is rushing away, but really, they’re just being winched out by the heavy-hitters outside our neighborhood.

The study suggests Earth and the Milky Way are drifting through a massive cosmic void spanning 2 billion light-years. This region contains significantly less matter than the rest of the universe. Because we are in this “empty” pocket, gravity from the denser universe outside the bubble is pulling galaxies away from us faster than normal.
If this theory is right, then we can say for sure that the universe isn’t breaking the laws of physics; we just happen to live in a weird, lonely neighborhood. In fact, the researchers calculate it is 100 times more likely that we reside in such a void than in a normal region.
It’s a humbling thought: We might be looking out at the universe from the inside of a giant cosmic ghost town, wondering why everything is running away from us so fast.